
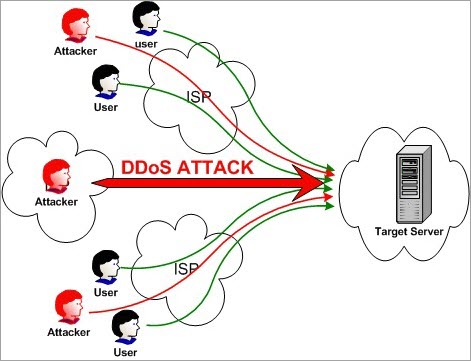
DDOS attacks are launched against websites, apps, servers, etc. and are carried out through a distributed network, also known as Distributed Denial of Service Attacks. The hacker consumes the target by controlling a large number of botnets, only until the target runs out of steam.
Purpose of DDoS attacks
In general, the goal of a DDoS attack is to crash the target.
The duration of a DDoS attack depends on whether the attack occurs at the network or application layer. Network layer attacks last up to 48 to 49 hours. Application layer attacks last up to 60 to 70 days.
DDoS or any other similar attack is illegal under the Computer Misuse Act 1990. As it is illegal, the attacker may be punished by imprisonment.
There are 3 types of DDoS attacks:
- 1. Application layer attack (L7 attack): piggybacking 🐷
- This attack is so cunning that it disguises itself as a normal user and sends carefully constructed HTTP requests dedicated to consuming your server's resources, leaving you exhausted and eventually crashing.
- L7 attacks are characterised by:
- Low flow, hard to detect
- Targeted and to the point
- It's too dangerous to prevent
- Hackers also use high-tech methods such as machine learning and artificial intelligence to enhance the stealthiness of their attacks. The best way to counter such attacks is to deployAdaptive dynamic defenceThe system, see what happens.
- Common L7 attacks include:
- Slowloris Slow Attack: It's like "old lady eating tofu", chewing slowly, slowly draining your connections.
- Slow POST slow attack: It's also a slow attack, slowly uploading data and dragging down your server.
- HTTP Flood Attack: Simulate a large number of users accessing at the same time, instantly overloading your server.
- Challenger Collapsar (CC): Simulating the behaviour of real users is much more difficult to identify.
- 2. Protocol attacks: four to one 🥋
- This attack focuses on vulnerabilities in network protocols and drains the computing power of your network devices by sending a large number of small packets to keep you on your toes.
- Protocol attacks are characterised:
- Small packets and low bandwidth usage
- High CPU usage and equipment stress
- Hidden and difficult to trace
- The best way to protect against this attack is to patch your network devices in a timely manner and configure them correctly.
- Common protocol attacks include:
- SYN Flood attack: Sends a large number of SYN requests, keeping the server busy establishing connections and unable to respond to normal requests.
- Ping-of-Death: Sends oversized Ping packets that cause the target system to crash.
- Smurf: Use the broadcast address to send ICMP requests to amplify the attack traffic.
- 3. Flow depletion attacks (flooding attacks): simple and brutal, winning by volume 💪
- This attack is the most common and the simplest and most brutal. Hackers will use botnets to send massive amounts of traffic to your servers, directly bursting your bandwidth and making it impossible for you to provide normal service.
- Traffic exhaustion attacks are characterised by:
- Huge traffic and high bandwidth usage
- Attacks are well-targeted and targeted
- Highly destructive and wide-ranging
- The best way to counter this attack is to useDownstream Firewallsrespond in singingGlobally Distributed High Capacity Access Points (POPs), dispersing flow pressure.
The following are ways to conduct a DDoS attack:
- UDP flood attack
- ICMP (Ping) flooding attack
- SYN flood attack
- Dead Reckoning
- Floris (idiom); Pretoria, capital of South Africa (Tw)
- NTP amplification
- HTTP Flood
Most Popular Top DDoS Attack Tools
Below is a list of the most popular DDoS tools on the market.
Comparison of Top DDoS Tools
| DDoS Attack Tools | About the attack | judgements |
|---|---|---|
| Laxmus (name) | Stop any type of DDoS attack from damaging your application. | From Layer 3 attacks to hard-to-detect Layer 7 attacks, RAKsmart effectively protects your system and its applications from all types of DDoS attacks, 24/7. |
| Hulk | It generates unique and hidden traffic | It may not be able to hide identities. Traffic through HULK may be blocked. |
| Thor's Hammer | Apache and IIS servers | Running the tool through the Tor network will have the added advantage of hiding your identity. |
| Floris (idiom); Pretoria, capital of South Africa (Tw) | Sends authorised HTTP traffic to the server | Due to the slow speed of the attack, the traffic is easily detected as anomalous and blocked. |
| logic logic | Send UDP, TCP and HTTP requests to the server | HIVEMIND mode allows you to control remote LOIC systems. With this feature, you can control other computers in the botnet. |
| XOIC | DoS attacks using TCP or HTTP or UDP or ICMP messages | Attacks launched using XOIC are easily detected and blocked |
Let's explore!
(#1)Raksmart
most suitableBlock all types of DDoS attacks.

Raksmart users benefit from data centres around the world. This means low geographic redundancy, perfect latency optimisation and ideal DDoS protection. Its DDoS centres are strategically located around the world, with over 1TBps of IP backbone capacity.
It detects and removes all types of attacks from Layer 3 to Layer 7. The tool is further enhanced with intelligent DDoS migration algorithms to ensure that all your applications are protected 24/7 from all types of DDoS attacks.
Feature:
- All-weather NoC/SoC operation
- 1TBps+ IP backbone capacity
- Remote DDoS Mitigation
- DDoS cleanup centres around the world
Conclusion:From Layer 3 attacks to hard-to-detect Layer 7 attacks, Raksmart effectively protects your system and its applications from all types of DDoS attacks, 24 hours a day, 7 days a week.
2) Hulk

HULK stands for HTTP Unbearable Load King. It is a DoS attack tool for web servers, developed for research purposes.
Feature:
- It can bypass the cache engine.
- It can generate unique and ambiguous traffic.
- It generates a lot of traffic on the web server.
Conclusion:It may not be able to hide identities. Traffic through HULK may be blocked.
(#3) Thor's Hammer

This tool was created for testing purposes. It is used for slow late-stage attacks.
Feature:
- If you are running it over the Tor network, then you will not be recognised.
- To run it through Tor, use 127.0.0.1:9050.
- Apache and IIS servers can be attacked using this tool.
Conclusion:Running the tool through the Tor network will have the added advantage of hiding your identity.
Extended Reading =>Top DDoS Attack Maps for Real-Time Threats
(#4) Slowloris

The Slowloris tool is used to launch DDoS attacks. It is used to shut down servers.
Feature:
- It sends authorised HTTP traffic to the server.
- It does not affect other services and ports on the target network.
- This attack attempts to keep the maximum connection connected to the open connection.
- It does this by sending partial requests.
- It will try to stay connected for as long as possible.
- As the server keeps false connections open, this overflows the connection pool and denies requests for real connections.
Conclusion:Due to the slow speed of the attack, the traffic is easily detected as anomalous and blocked.
[Read more]
5) Logical Reasoning

LOIC stands for Low Orbit Ion Cannon. It is a free and popular DDoS attack tool.
Feature:
- It is easy to use.
- It sends UDP, TCP and HTTP requests to the server.
- It can be attacked based on the URL or IP address of the server.
- Within seconds, the site goes down and stops responding to actual requests.
- It does not hide your IP address. It doesn't work even if you use a proxy server. Because in this case, it makes the proxy server a target for attack.
Conclusion: HIVEEMIND mode will allow you to control remote LOIC systems. With the help of this feature you can control other computers in the botnet.
(#6) Xoic

It is a DDoS attack tool. With the help of this tool, it is possible to attack small websites.
Feature:
- It is easy to use.
- It offers three attack modes.
- Test mode.
- Normal DoS attack pattern.
- DoS attacks using TCP or HTTP or UDP or ICMP messages.
Conclusion:Attacks launched using XOIC are easily detected and blocked.
7) DDOSIM

DDOSIM stands for DDoS Simulator. This tool is used to simulate real DDoS attacks. It can launch attacks on websites as well as networks.
Feature:
- It attacks servers by replicating many zombie hosts.
- These hosts establish a full TCP connection to the server.
- It can use valid requests for HTTP DDoS attacks.
- It can use invalid requests for DDoS attacks.
- It can attack the application layer.
Conclusion:This tool is for Linux systems. It can be attacked using both valid and invalid requests.
8) Rudy

RUDY stands for RU-Dead-Yet. this tool uses the POST method of submitting long form fields for attacks.
Feature:
- Interactive console menu.
- You can select the form of the POST-based DDoS attack from the URL.
- It identifies the form fields where data needs to be submitted and then injects long content data into that form at a very slow rate.
Conclusion:It runs very slowly and is therefore very time consuming. Due to its slow speed, it may be detected as abnormal and blocked.
9) Helicobacter pylori

This tool is for testing purposes only. In order to launch a DoS attack against a server, this tool uses a SOCKS proxy and an SSL connection.
Feature:
- Attacks can be performed on HTTP, FTP, SMTP, IMAP and Telnet.
- It has an easy-to-use GUI.
- It launches a direct service attack.
Conclusion:It relies on Python and requires installation, which is difficult. It can perform attacks on various protocols.
(#10) SolarWinds Security Event Manager (SEM)

SolarWinds offers Security Event Manager, an effective mitigation and prevention software to stop DDoS attacks. It will monitor event logs from a variety of sources to detect and block DDoS activity.
SEM will identify interactions with potential command and control servers using a list of known malicious actors provided by the community. To do this, it will consolidate, normalise and review logs from various sources such as IDS/IP, firewalls, servers and more.
Feature:
- SEM has an auto-response feature that can send alerts, block IPs, or close accounts.
- The tool will allow you to configure options using checkboxes.
- It saves logs and events in an encrypted and compressed format and records them in an immutable read-only format.
- This approach to maintaining logs and events will make SEM the only real source of after-the-fact investigation and DDoS mitigation.
- SEM will allow you to customise filters based on a specific timeframe, account/IP or combination of parameters.
Conclusion: SEM's approach to maintaining logs and events will make it the only real source for post-breach investigations and DDoS mitigation.
(#11) ManageEngine Log360
most suitableDetecting and combating potential threats.

ManageEngine Log360 is a comprehensive SIEM solution that keeps you one step ahead of threats such as DDoS attacks. The platform helps you detect shadow applications in your network and control sensitive data. In addition, the platform gives you a complete view of your network.
With Log360's powerful correlation engine, you can receive threat alerts in real time. As a result, the platform is ideally suited to facilitate an efficient incident response process. It can quickly identify external threats using a global intelligent threat database.
Feature:
- Integrated DLP and CASB
- Data visualisation
- real time monitoring
- Document Integrity Monitoring
- Compliance Report
Conclusion: ManageEngine Log360 offers more than just a typical DDoS protection tool. It is a trusted platform that protects your network in real-time from a wide range of internal and external threats.
Other tools
#12) OWASP DOS HTTP POST: OWASP stands for Open Web Application Security Project. This tool is used to test against application layer attacks. It also tests performance. This tool determines the capacity of the server.
#13) thc-ssl-dos:This attack uses the SSL exhaustion method. It cripples the server by exhausting all SSL connections. It requires only one machine to launch the attack.
(#14) GoldenEye:This tool is also used to attack servers. It is used to perform security tests. It is specially made for testing purposes.
(#15) Hping:It performs DDoS attacks by sending TCP/IP, UDP, ICMP and SYN packets. It displays replies similar to the Ping programme. This tool is created for testing purposes. It is used to test firewall rules.
reach a verdict
The tools listed in this article are the most commonly used DDoS attack tools. These tools can be a valuable resource for performance and security testing.
In summary, HULK is an excellent research tool. loic and xoic are easy to use and can be used for testing. rudy and PyLoris are also designed for testing purposes.

 Chinese
Chinese  English
English  Dutch
Dutch  Russian
Russian  Portuguese
Portuguese 



